Three years ago, I switched from LastPass to Bitwarden for password management, mainly because there were features Bitwarden had that LastPass did not. One of the “features” I was not expecting, however, was the misleading export interface.
Bitwarden refers to its encrypted space as the Vault, and the logins, passwords, etc. that users store as Vault Items,
There are 4 types of items you can store in your Vault; Logins, Cards, Identities, and Secure Notes
Bitwarden provides options to export a vault for backup or other purposes.
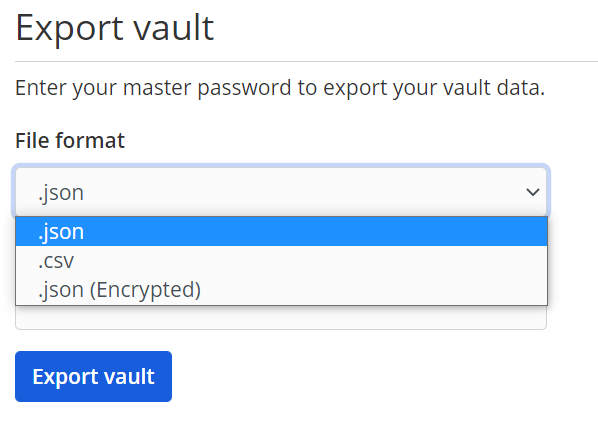
There are two problems with this interface.
- Although the user is lead to believe that they are exporting their vault, not all items in the vault are exported if the user choose CSV. Specifically, even though Cards and Identities are clearly list as two of the four item types in a vault, they are not included in a CSV export.
- Attachments are not exported with any of the export options. As far as I can tell, there is no way to get a backup of attachments at all from the Bitwarden web vault without going through each item individually and manually saving the attachments.
This is documented in the Bitwarden help article on exports, but these sorts of omissions should be made clear front and center on the Export Vault page itself.
Even better, Bitwarden should just fix this. There are feature requests going back to 2018 that highlight the potential problems created by not having a method of exporting attachments from Bitwarden. As one user puts it,
It’s now JSON. Base64 encoding would work. This is a really annoying thing to miss. I really thought I had a full backup of my stuff until I saw the JSON is unexpectedly small given the attachments I’ve stored in BW. I use this to sync between two different BW accounts (paid one here, and my privately hosted one). Only it’s not really syncing, if the attachments are missing. These are scans of identity documents, private keys for PGP.
I understand this may be an issue for people who have huge amounts of attachments due to the size of the resulting JSON, but simply omitting them is not a solution. If that’s the concern, make it optional or filter by size or something.
The odd thing is that this doesn’t seem to be that big of an issue to resolve. Caesar Kabalan ran into the same problem and created a Github repository with a Bash script that exports an encrypted file containing all Bitwarden attachments using the Bitwarden CLI. But this process is only an option for pretty advanced users.