Mmmm . . . a paper Enigma machine you can download as a PDF, print and assemble.
Tag: Encryption
Serious Google Calendar Encryption with GnuPGP
IBM’s Nathan Harrington has written an article outlining how to use the GnuPGP Firefox extension to create encrypted events within Google Calendar. This isn’t just accessing Google Calendar securely, but rather encrypting event details locally before passing that text on to Google Calendar. Anyone who compromises your Google account then would know the time of events, but would only see encrypted text for the actual event detail as in the example below,
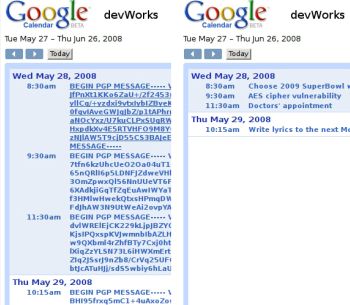
That is frackin’ awesome. Now if there were only a GnuPGP plugin for my Blackberry calendar so I could sync the events meaningfully.
TrueCrypt Deniable File System Broken
The other day, Bruce Schneier had some post about securing data for border crossings and in the comments someone asked why not just use TrueCrypt’s deniable file system, which in TrueCrypt’s implementation hides an encrypted file system within a TrueCrypt encrypted volume. Schneier responded that he didn’t trust TrueCrypt’s deniable file system, and today he reveals why — he and several other researchers are publishing a paper announcing they were able to break that particular feature of TrueCrypt.
ABSTRACT: We examine the security requirements for creating a Deniable File System (DFS), and the efficacy with which the TrueCrypt disk-encryption software meets those requirements. We find that the Windows Vista operating system itself, Microsoft Word, and Google Desktop all compromise the deniability of a TrueCrypt DFS. While staged in the context of TrueCrypt, our research highlights several fundamental challenges to the creation and use of any DFS: even when the file system may be deniable in the pure, mathematical sense, we find that the environment surrounding that file system can undermine its deniability, as well as its contents. Finally, we suggest approaches for overcoming these challenges on modern operating systems like Windows.
TrueCrypt has apparently addressed many of the specific issues raised by the paper in their 6.0 release, but Schneier’s claim is that there are inherent problems to creating a deniable file system so even though the techniques outlined in the paper will not work against TrueCrypt 6.0, even the deniable file system there should be treated as untrusted. Better to go with whole disk encryption, which loses the deniability but is more secure.
The entire paper is avaialble as a PDF download.
TrueCrypt 6.0
A new version of everyone’s favorite open source disk encryption software, TrueCrypt, has just been released. Version 6.0 has been optimized for mulit-core processors and includes a number of new features including the ability to use hidden volumes under OS X/Linux.
FireGPG
FireGPG is a GPLed Firefox extension that allows users to encrypt, decrypt, sign or verify the signature of text in any web page. The latest version, released in January 2008, includes a FireGPG API so it could be integrated into specific website (the developers’ focus is on web-based mail).
One-Click Opening of TrueCrypt Volumes
I’m a big fan and regular user of TrueCrypt, a completely free and open source program that creates virtual encrypted disks on Windows and Linux volumes. Like a lot of other such programs, however, mounting the encrypted volumes can get a bit tedious.
AllThingsMarked.Com has a nice tutorial on how to create a batch script to make it a lot easier to mount and unmount a TrueCrypt volume.
The one defect of the AllThingsMarked.Com approach is that it doesn’t mask the password during entry, but Peter Hesse has a slightly modified version of the AllThingsMarked.Com method that does mask the password as long as you’re running Windows XP or Windows Server 2003 or later.