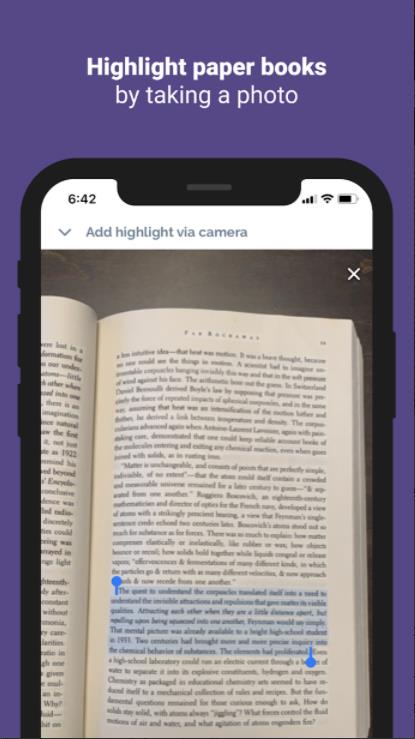
Readwise has an “early access” version of their Android app available.
One of the more intriguing planned features of the app is the ability to capture highlights in physical books by taking a photo of the book.
Just another nerd.
Readwise has an “early access” version of their Android app available.
One of the more intriguing planned features of the app is the ability to capture highlights in physical books by taking a photo of the book.

In non-COVID-19 news, Google is apparently going to start requiring manufacturers to implement its “seamless update” system beginning with Android 11.
Essentially, Android 11 will require devices to have a separate system partition that is an identical copy of the main partition. When an updated to Android is available, the update installs itself on the second partition. When that installation is finished, the phone is rebooted, and the secondary partition becomes the primary partition.
The intent here is to reduce the downtime that can come with some Android updates, as well as always having a good partition that can be booted to if an update goes awry.
The system partition, by the way, is apparently relatively small on a typical Android device–it clocked in at about 320 megabytes on the 2016 Pixel 1.
Back in 2018, Google announced that beginning with Android 9, it would prevent apps from using unencrypted connections by default. As of December 2019, Google notes that 80 percent of all apps in the Google Play store use TLS, and that rises to 90 percent of all apps targeting Android 9 and higher.
Android 7 (API level 24) introduced the Network Security Configuration in 2016, allowing app developers to configure the network security policy for their app through a declarative configuration file. To ensure apps are safe, apps targeting Android 9 (API level 28) or higher automatically have a policy set by default that prevents unencrypted traffic for every domain.
Today, we’re happy to announce that 80% of Android apps are encrypting traffic by default. The percentage is even greater for apps targeting Android 9 and higher, with 90% of them encrypting traffic by default.
Since November 1 2019, all app (updates as well as all new apps on Google Play) must target at least Android 9. As a result, we expect these numbers to continue improving. Network traffic from these apps is secure by default and any use of unencrypted connections is the result of an explicit choice by the developer.
That last sentence is a bit concerning. If app developers want to explicitly make their apps communicate through unencrypted connections, that’s fine, but as far as I can tell there is no way that consumers are made aware of this.
Just as modern browsers warn me that the website I’m visiting doesn’t use encryption, Google should inform users when they are using apps that do so as well. I’d be happy with a notification on the Google Play store page for such apps that “This app sends network traffic over unencrypted channels” or something like that.
(Yes, users could set up a packet analysis tool to look at the data their phone is sending, but they shouldn’t have to do so).
Inware is a free Android app that gives users detailed information about their mobile device with a well-designed user interface.
HTTrack Website Copier is a free, open source solution for making local mirrors of websites. What I didn’t realize until recently is that there is an Android version of the utility available on the Google Play Store.
It allows you to download a World Wide Web site from the Internet to a local directory, building recursively all directories, getting HTML, images, and other files from the server to your computer. HTTrack arranges the original site’s relative link-structure. Simply open a page of the “mirrored” website in your browser, and you can browse the site from link to link, as if you were viewing it online. HTTrack can also update an existing mirrored site, and resume interrupted downloads. HTTrack is fully configurable, and has an integrated help system.
Easy DND (Do Not Disturb) is an early access Android app designed to help users better manage Android’s increasingly complex array of do not disturb options. It is free, open source, and requires only a single permission (access to do not disturb settings).