The One-Time Password plugin for WordPress is probably overkill for most of us, but if you regularly need to login to WordPress from computers that you don’t control, this would certainly add an additional layer of security.
Tag: Security
BTProx – Use Your Bluetooth-Enabled Phone to Automatically Lock Your Windows PC
BTProx is an open source application for Windows that will automatically lock your Windows Desktop if your bluetooth-enabled cellphone is no longer nearby,
It locks on one of your Bluetooth devices which are paired to the the machine. When you walk away from the computer the device is disconnected and the computer is locked after timeout. It is possible to run a single application together with the lock. This application may be your favorite script dismounting network drives, erasing those dirty files from the desktop or anything else. The program sits in Windows tray showing its current status with tray icon and tooltip baloons.
That is an awesome idea. Hopefully someone will come up with something like this for OSX and Linux as well.
Update: BlueProximity for Linux accomplishes the same thing in Linux.
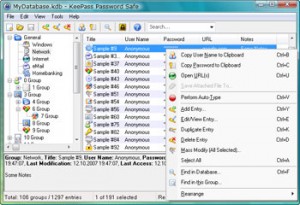
KeePass
A couple years ago I downloaded and tried the open source password manager KeePass, but ultimately passed on it in favor of RoboForm. The other day I decided to give it a second look since I needed something that was cross-platform.
After tinkering around with it for a few minutes I was sold. I can’t remember why I didn’t like it a couple years ago, but whatever it was they’ve certainly fixed it several times over.
What I especially like about KeePass is the cross platform nature of it. I’ve got it running on my Windows and Ubuntu PCs as well as my Blackberry. For the moment, I update my database on my home server and then upload it to an obscure directory on my dedicated web server. Then its just a matter of installing KeePass on any computer I want to use at downloading the database.
KeePass does a nice job of autotyping. Just put the cursor in the username field, press CTRL-ALT-A and it will find the correct password for the site in the database and fill in the username and password fields.
Someone has written a nice plugin for KeePass 2.x, which is still in Alpha, that will synchronize the database over the Internet (though its unclear if this will work with vanilla FTP/SFTP).
Blizzard Announces a Physical Token for World of Warcraft Account Authentication
 Theft of World of Warcraft accounts is a huge problem. The perception is that gold farmers are finding it much more lucrative to simply hack people’s accounts by tricking them into to installing keyloggers rather than actually use in-game bots to farm resources. There is an entire class of trojans now aimed largely at WoW players.
Theft of World of Warcraft accounts is a huge problem. The perception is that gold farmers are finding it much more lucrative to simply hack people’s accounts by tricking them into to installing keyloggers rather than actually use in-game bots to farm resources. There is an entire class of trojans now aimed largely at WoW players.
So Blizzard recently announced a forthcoming Authenticator product which looks to be a rebranded RSA SecurID. The device will costs $6.50 and asks the user to link the serial number of the device to the WoW account. From then on, when you want to log in you enter your username and password, then press a button on the Authenticator which generates a number that has to be entered as well. The number is essentially a rolling one time pad, and that specific number is only good for 30-60 seconds. So someone who manages to grab all three pieces of data has a very small window in which to gain access to your account.
As some have noted on WoW-related sites, this sort of scheme is still vulnerable to man-in-the-middle attacks. Think of this being used to authenticate login to a bank website. I put my server in between you and the bank. You think your data is going to the bank, but its really going to my server, then I’m passing it on to the bank, and then passing the bank’s response on to you. You never even know you’ve been hacked until I log in with your password and ID later and clean out everything.
Assuming that the Authenticator is ever owned by a large percentage of users — and I’m skeptical it will be — it will be interesting to see if the hackers turn to man-in-the-middle style attacks or simply turn their attention to an easier target.
Tips for Increasing WordPress Security
Noupe.Com has a nice list of tips for making a WordPress install more secure.
Lousy Security from Phone Conferencing Companies
The other day I was assisting a group that needed to attend one of these “webinars” where we’re projecting a laptop onto a screen while we’re listening to a speaker over a POTS line. As the e-mail from the company sponsoring the webinar suggested, I dialed in about 20 minutes before the conference started to test, etc.
Except I wasn’t dumped into the conference I was supposed to be in. Instead I was now participating in some sort of briefing between salesman at a company that provides services to a number of large insurance companies. The salesmen could not hear me and were apparently completely unaware of my presence as they discussed the best approach to take with a particular client, and one chimed in with a list of things not to say during another.
Finally at the appointed time my call was supposed to start, the salespeople all hung up and the person from the company I was conferencing with was added to the call.
Now typically the security for these calls is you have to call a phone number and then enter an arbitrary number that corresponds to your particular call. So there are likely two possibilities for the mishap.
First, the people at the conference company could be complete morons and use a single ID # for a single conference slot and then give that conference ID out to different people, assuming they won’t call in outside their normally scheduled time.
Another possibility is that the algorithm the company is using to generate conference ID # is flawed and doesn’t generate truly unique IDs. One of the things I noticed is that with most audio conference companies I use, I typically get a 9-12 digit code for the conference, whereas these folks only used a 6 digit code which struck me as kind of odd.
Regardless if it was something like this or something completely different, this sort of thing is completely unacceptable and should never happen. I had never used this particular company before and certainly will warn other people in my organization about them.
Given how important security is in third party hosted audio/video conferencing, its surprising how cavalier some companies are about security.