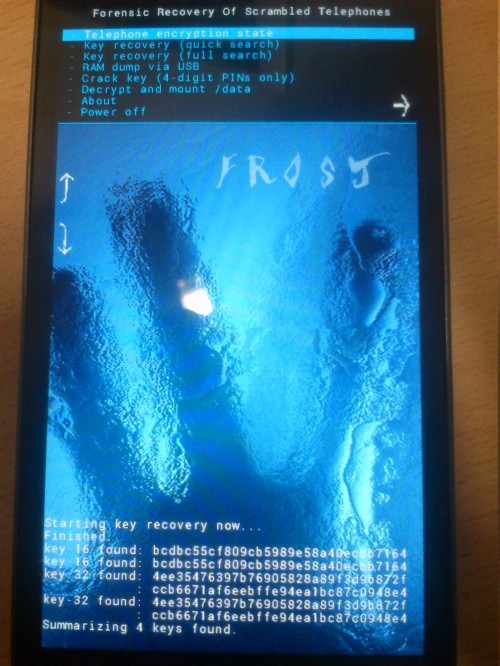
Researchers at Erlangen University in Germany have demonstrated a cold boot attack against Android phones. Princeton researchers originally first demonstrated cold boot attacks in PCs. The DRAM in most computers (and mobile phones) will retain data for up to a few seconds after a device is shut off, and the period of time the data is retained can be extended significantly by lowering its temperature.
In the mobile device cold boot attack, the researchers put Android phones in a freezer that was -15 degrees Celsius, and left the device for an hour until its temperature fell below 10 degrees Celsius. The researchers then forced the phone to reboot into Android’s fastboot mode which allowed them to run their code to scan for encryption keys in RAM, contacts, photographs, etc. that survived the rebooting thanks to the extremely low temperature of the phone.
One oddity here is that while they were able to recover data from phones that had their boot loader unlocked and phones that still had the boot loader locked, they were only able to recover the full disk encryption keys from the unlocked phones,
To break disk encryption, the bootloader must be unlocked before the attack because scrambled user partitions are wiped during unlocking.
So at least for this sort of attack, you’re better off with a locked phone.